Windows 침해 대응 및 분석 기법 ( 금융보안원 교육 )

과거의 공격양상 (약.. 10년전..?) exe 또는 dll 확장자 파일을 통해 함수 호출 변수를 통한 C&C에서로의 공격을 감행함
하지만 안티바이러스에서 다 검출되기에 현재는 이런 재래식 형태로 공격을 감행하지 않음.
그래서 LotL(Living of the Land) 공격기법 --> 기존의 있는 시료들을 통해 공격을 감행하는 기법
wscrpite.exe, certutil.exe 등 기존의 Windows Built in 설치 파일을 통한 공격 감행 형태로 양상 변형
최근 공격 형태의 양상
1.악성 문서 파일 생성
2.공격자는 Victim PC 에 악성문서 전달
3. maleware.hwp 문서파일 통해 한글 오피스 프로그램 실행됨
maleware.hwp 실행 시,
유관된 dll 파일을 메모리에 적재함 (무수히 많은 dll 을 호출하며 프로세싱을 함)
이 시점에서 dll파일을 호출하는게 아닌 건너뛰고 다른 메모리 영역을 통해 Powershell 호출함
※ 가상 메모리 공간
( 커널 메모리 - 주요 자료 영역구역 / 유저 메모리 영역 - 각각의 프로세스들이 가상의 격리된 영역을 갖음 )
메모리가 허용하는 만큼 가상의 메모리 공간을 가짐
해당문서의 내부에는 쉘코드(악성코드)가 삽입되어 공격자의 C&C 서버와 통신하며 공격자의 흐름대로 움직임.
공격자코드 : 인터넷 경로의 어디어디로가면 script가 있어 그걸 호출해
정상적인 프로세스 explore.exe 애들한테 code injection을 실시
다른 프로세스의 메모리상에다가 악성프로세스를 주입
그럼 악성프로세스가 C&C 서버와 통신함 (이때 Powershell 은 0.1초만 잠깐 실행되었다가 닫힘 )
사용자 입장에서는 변화 체감 못함
이것을 우리는 파일리스 공격( Fileleass Attack )이라고 부름
감염 PC로 의심되면 다음과 같은 행동이 필요함.
🔍 1. 아티팩트 (디지털 증거) 수집
컬렉션 도구를 외장 USB를 통해 Victim PC 에 옮겨둠
그 내용을 가지고서 분석관 PC 로 옮겨 피해내용 분석 진행
※ 피해 PC에서는 가급적이면 분석하지 X
--> 그 이유는 Victim PC의 프로세스 함수 호출을 하며 메모리 변화 시스템 변화가 일어나기 때문에
해당 PC의 상태변화를 촉구함, 최대한 해당 PC를 원상태로 두기 위함임.
프로세스 리스트 확보
tasklist /SVC > tasklist.txt모든 프로세스는 실행 후 반드시 서비스를 책임져야함
서비스를 책임지는 프로세스가 없다 ( EX. N/A로 표시된다면 악성코드일 확률이 높음 )
listdlls 프로그램 통한 DLL파일 확보 ( sysinternals suite )
sysinternals 에서 만듬
listdlls -u
--> u 옵션은 unsigned 된 DLL 만 확인하여 검출함
이 옵션때문에 sysinternal 을 쓰는거임 ( 서명정보가 없거나 누락된 파일을 확인 하기 위함임 )
파일을 실행할때 서명정보가 존재하지 않는다면 경고가 올라옴
MS 한테 악성코드를 매번 서명정보를 받아오기는 힘들기 때문에 해당 파일을 수집하는거임
Persistence (제어지속정보)
공격자는 원하는 시간에 공격하길 희망함
그래서 지속적으로 공격자가 자동으로 시작되게 만든 프로세스를 찾아야함..!
sysinternals - Autoruns 통해 확인
파일 시스템 관련 증거 수집 ( HBGary's fget 도구 활용 )
※ 환경변수에 설정해주어서 편하게 실행하자 !!!
raw 한 파일시스템 확이 가능
Windows Prefetch 파일 실행 이력 확인
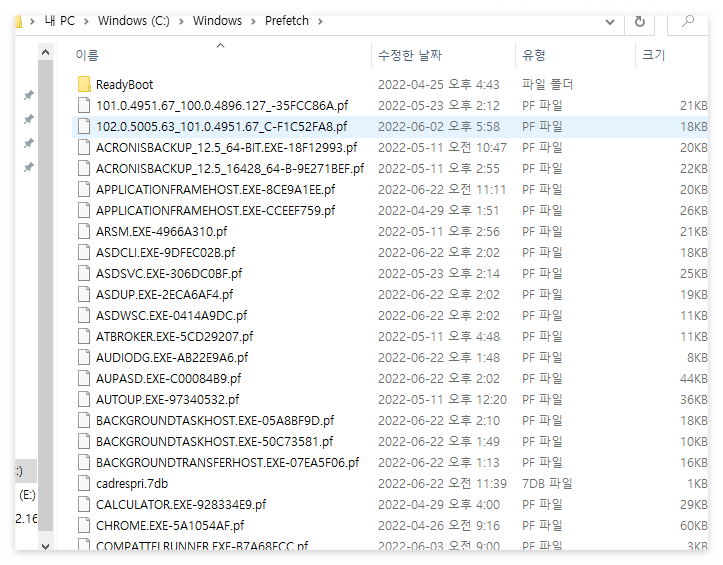
pf 목록열을 확인하면 exe파일의 파일들이 나옴
해당 파일들은 한번이라도 이 PC에서 실행했던 파일명이라고 알수있음
Memory Dump
Dumpit.exe 파일 실행 후 메모리 덤프를 뜰 수 있음
Registry 수정 내용 확인
리눅스의 /etc 폴더와 같은역할임
시스템의 전반적인 환경변수 설정들을 담고있음
C:\Windows\System32\config 에 해당 설정 파일들이 있음
SAM --> 윈도우의 비밀번호
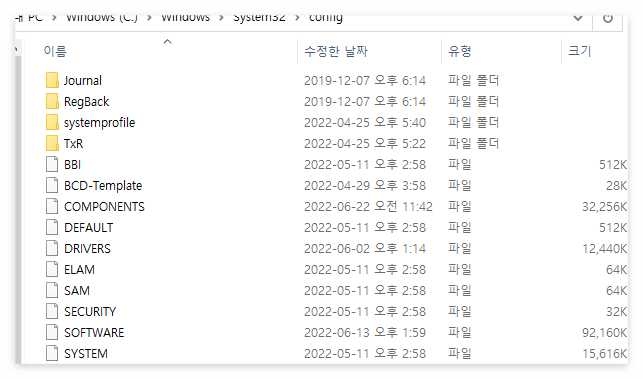
파일이란
프로세스들이 로딩한 목록들이 나옴
📊 2. 분석 담당자 PC에서 확인
volatility 파일 통해 메모리덤프 확인
처음 사용시 OS 버전을 확인시켜줘야함
해당 메모리 덤프를 통해 PID // PPID 확인 가능
※ PPID : 부모 프로세스
pslist
DLLList
Netscan
## 메모리 덤프를 통해 OS 윈도우 이미지 정보 확인 ##
vola -f memory.raw imageinfo
vola -f memory.raw --profile=Win7SP0X86 pslist > .\volataility_pslist.txt
vola -f memory.raw --profile=Win7SP0X86 netscan > .\volataility_netscan.txt
vola -f memory.raw --profile=Win7SP0X86 dlllist > .\volataility_dlllist.txt
상기 3개의 명령어를 통해 Windows Built-In 파일 중 절대 Network 트랙잭션이 일어나지 않아야할 파일이 통신이 이루어진 이력이 있다면 해당 파일은 코드인젝션이 일어났을 수 있다는 가능성을 제기 할 수 있음.
AnalyzeMFT.py 통한 mft.raw 파일분석
python analyzeMFT.py -l -f mft.raw -o -mft.csv
👣 3. 분석 (Interpretation)
악성 프로세스 식별 방법
1) 정상 프로세스와 유사한 이름을 사용하는 프로세스가 존재하는지
2) 프로세스의 부모자식 관계에서 이상징후가 보이는지
3) 서비스를 제공해야 할 프로세스가 서비스를 제공하지 않는지
4) 실행 경로가 일반적이지 않은 경우가 있는지
C:/Windows --> 정상 경로
C:/Windows/system32/explorer.exe --> 잘못된 경로 // 악성코드 의심
C:/Users/사용자명/AppData/Local/Temp/ --> 임시 경로 // 악성코드 의심
일반적으로 C:/Windows or C:\Program Files 의 경로에서 대부분의 프로그램들이 실행이 됨.
그렇다면 그렇지 않은경로에서 프로그램이 실행된 이력이 있는지 검출 하면 됨.
5) 본래의 기능과는 다르게 네트워크 통신을 수행하는 프로세스가 있는지
윈도우 운영체제에서는 Network 통신을 하지 않는 프로세스들이 있음.
--> 해당 내용은 확인 해보길
6) 정상적인 프로세스이지만 종료 되어 있어야 함에도 동작하고 있는 프로세스가 있는지
EX) userinit.exe (사용자 로그인 후 환경 초기화 후 바로 종료함, 해당 프로세스가 explorer.exe 호출)
7) 서명이 되어 있지 않은 exe or DLL 이 실행되고 있는 경우가 있는지
listdlls_unsigned 통해 아래의 의심스러움 확인
C:\Program Files\SearchNQ\SearchNQ.exe
C:\Windows\system32\svcnet.exe
※ 악성코드 분석은 격리된 환경에서 수행하고, 분석관은 악성코드 Malicious File 을 보통 Hash값으로 변경함
악성 프로세스 식별 방법
1) 정상 프로세스와 유사한 이름을 사용하는 프로세스가 존재하는가
svchost.exe (O)
svch0st.exe (X)
scvhost.exe (X)
--> 사용자를 눈속임 하기위함
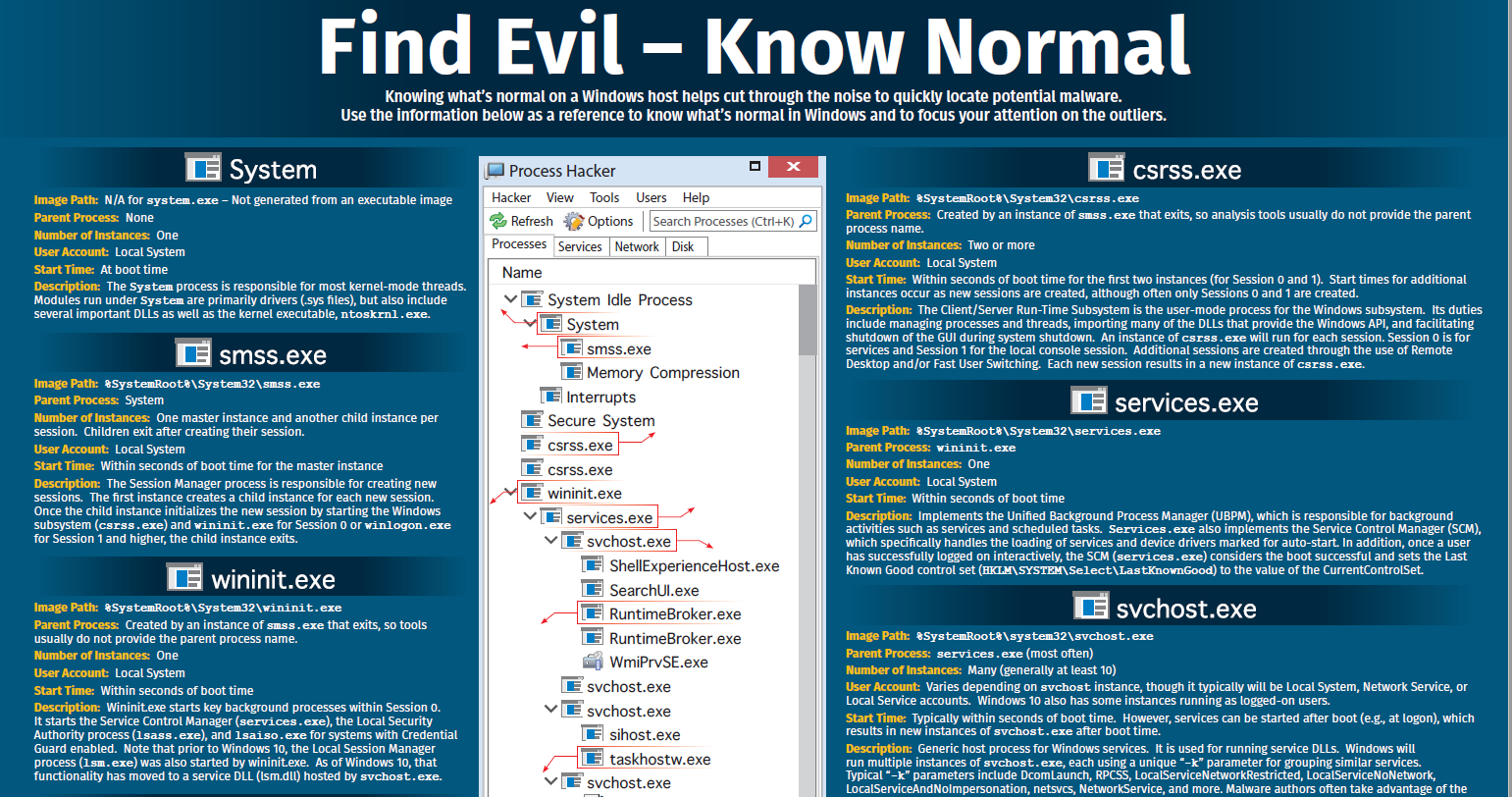
정상프로세스에 대한 판별은 ?
아래의 하기 문건을 참조하면 됨
링크참조 : Hunt Evil | SANS Poster
KALILINUX 와 상반적으로 방어용 우분투 OS 분석용 OS는 REMNux 패키징 오픈소스가 있음
링크 : REMnux: A Linux Toolkit for Malware Analysts
REMnux: A Linux Toolkit for Malware Analysts
REMnux: A Linux Toolkit for Malware Analysis REMnux® is a Linux toolkit for reverse-engineering and analyzing malicious software. REMnux provides a curated collection of free tools created by the community. Analysts can use it to investigate malware witho
remnux.org
모바일 방어 및 취약점 분석은 아래의
링크 : Download · Santoku Linux (santoku-linux.com)
Download · Santoku Linux
Santoku Community Edition runs in the lightweight Lubuntu Linux distro. It can be run in VirtualBox (recommended) or VMWare Player, both available free and run on Linux, Mac or Windows. The Lubuntu download is large because it is a full .iso. We recommend
santoku-linux.com
상기의 배포용 패키징 OS는 SANS라는 보안회사에서 만들었음
2) 프로세스의 부모자식 관계에서 이상징후가 보이는지
Services.exe - svchost.exe ( 정상 )
explorer.exe - cmd.exe ( 정상 )
rundll32.exe - powershell.exe ( 비정상 )
powershell.exe - dllhost.exe ( 비정상 )
DLLHOST의 부모프로세스는 svchost.exe 임.
svchost.exe - dllhost.exe ( 정상 )
## svchost의 프로세스 리스트 ##
C:\Users\fsiedu>tasklist /SVC | findstr svchost | moresvchost.exe 프로세스가 서비스를 제공하고 있지 않는지 확인
svchost.exe 프로세스가 파라미터를 가지지 않는지 확인
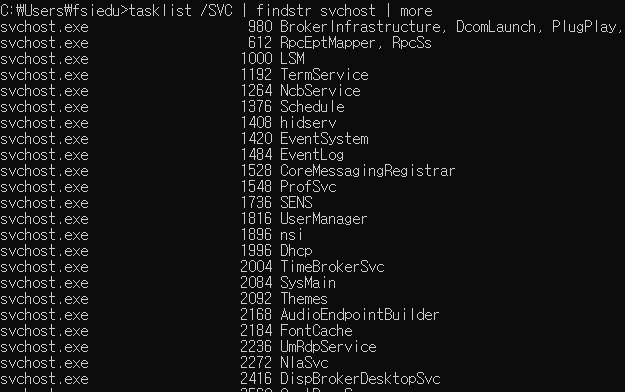
-k Parameter를 통해 svchsot에 서비스를 적재하고 서비스가 프로세싱됨
이런 Parameter가 없다면 악성코드로 판단할 수 있음.

explorer.EXE --> GUI 의 인터페이스를 관장하는 셸 프로세스
이것을 수시로 분석하기 위해서는 EDR 솔루션이 필요함.
제어 유지 방식
1. Registry ( 레지스트리 )
레지스트리 목록 구조 / 역할들을 알아야함
2. Task schedule ( 작업스케줄러 )
3. 시작 폴더
- Win + R > shell:startup
엔트리포인트란 무엇인가..?
파일구조는 [VBR / MFT / DATA] --> 이런 구조
MFT ( Master File Table )안에는
[MFT / MFT Entry / ]
WinprefetchView --> 통해 최근 실행 파일 흔적 확인
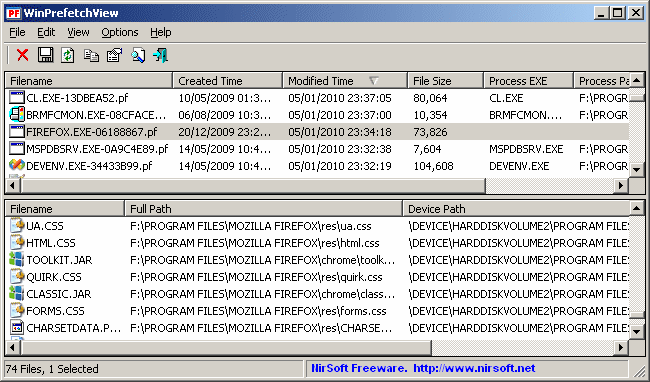
Run Count : 1
보통 악성코드는 최초 1~2회 실행되니 확인해볼것
Missing Process
현재 그파일이 존재하는지 여부 확인
Yes : 없어짐
No : 현재도 존재
[UserAssist]
사용자가 실제로 실행한 파일
디지털 포렌식 아티팩트 & 증거 분석 기법 공유 | 인섹시큐리티 (forensic-artifact.com)
디지털 포렌식 아티팩트 & 증거 분석 기법 공유 | 인섹시큐리티
[증거]테이블의 상단 칼럼 정보를 통해 사용자 이름, 응용프로그램 이름, 마지막 실행 시간, 실행 횟수 정보를 확인 할 수 있고 우측 [세부 정보]테이블을 통해서도 확인 가능
www.forensic-artifact.com
NirSoft - freeware utilities: password recovery, system utilities, desktop utilities
freeware utilities: password recovery, system utilities, desktop utilities - For Windows
Unique collection of freeware desktop utilities, system utilities, password recovery tools, and more
www.nirsoft.net
메모리 덤프
vlola.exe -f mft.raw --profile=[운영체제_Version] [추출할 데이터] > [추출데이터].txt
vlola.exe -f mft.raw --profile=Win7SPx86 dlllist > dlllist.txt
vlola.exe -f mft.raw --profile=Win7SPx86 malfind > malfind.txt
vlola.exe -f mft.raw --profile=Win7SPx86 pslist > pslist.txt
OpenProcess(PID) : 표적 프로세스 핸들확보
VirtualAllocEx(200) : 표적프로세스에 메모리 할당
WriteProcessMemory() : 표적 프로세스의 메모리에 악성 데이터 쓰기
CreateRemoteThread() : 표적 프로세스애 쓰레드 생성
메모리덤프 공부하기
--> vola 통해서 해당 메모리 덤프 확인가능
프로세스 인젝션 공부
Ten process injection techniques: A technical survey of common and trending process injection techniques
Process injection is a widespread defense evasion technique employed often within malware and fileless adversary tradecraft, and entails running custom code within the address space of another process. Process injection improves stealth, and some technique
www.elastic.co
자동화 도구
You are being redirected...
www.brimorlabs.com
Live Response Collection – Cedarpelta Build
- 여러개의 스탠드 얼론 실행 파일을 배치 스크립트를 통해 실행
- 노이즈가 심하다는 단점 아티팩트 원본을 충실하게 확보함
- Collection + Extraction(일부) 까지 수행함
Fireeye's Redline
-별도의 아티팩트를 수집 스크립트를 생성함
-수집된 아티팩트를 대상으로 분석하여 GUI 로 보여줌
- 근데 느림..